According to IT security vendors Kaspersky Lab, the Tor anonymity network is under threat of being swamped by criminals abusing the anonymity it provides for hiding zombie networks, malicious command and control servers and ‘darknets’, Le Monde Informatique reports.
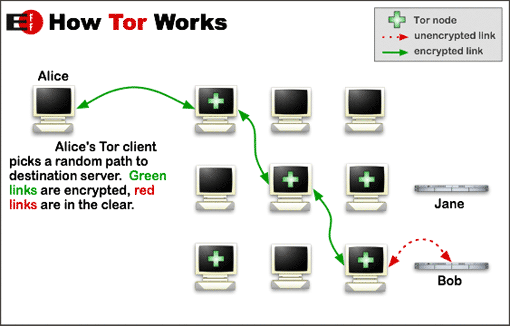
Tor – otherwise known as The Onion Router – has always had its dark side, but last year the network’s use by criminals seems to have grown appreciably. According to researcher Sergey Lozhkin, “Kaspersky Lab had uncovered evidence of 900 services using Tor, equivalent to 5,500 nodes (server relays) and 1,000 exit nodes (servers from which traffic emerges) in total.”
“It all started from the notorious Silk Road market and evolved into dozens of specialist markets: drugs, arms and, of course, malware.
“Carding shops are firmly established in the Darknet. Stolen personal info is for sale with a wide variety of search attributes like country, bank, etc. Offers for customers of this kind are not limited to credit cards. Dumps, skimmers and carding equipment are for sale too”, he added.
“In addition, command and control (C&C) servers hosted by Tor are more difficult to flush out, blacklist or eliminate,” Lozhkin continued. “Although creating a Tor communication module within a malware sample means extra work for the malware developers. We expect there will be a rise in new Tor-based malware, as well as Tor support for existing malware.”
Experts from Kaspersky Lab have so far found Zeus with Tor capabilities and then detected ChewBacca and finally analysed the first Tor Trojan for Android.